Instant Protection PLUS 3 has the ability to "lock" your software to the computer on which it is activated. By taking a "fingerprint" of certain hardware pieces of the computer during activation and storing this fingerprint (or Computer ID) in the license file, the application can verify the Computer ID on subsequent executions in order to determine if it is still running on the same computer. This mechanism stops a user from activating the application and copying it to multiple computers still fully activated. There are two Computer ID implementations in Instant Protection PLUS 3: Legacy Computer ID Algorithms and Enhanced Computer ID Algorithms.
Copy-Protection involves your application obtaining identification information about the system on which it is running. Typically, any license which requires activation uses information about the system so that the specific system may be authorized. Instant Protection PLUS 3 assists you with authorizing and validating this information by making identifier algorithms available to you. The Enhanced Computer ID Algorithms can be used to generate "System Identifiers" using any combination of information including (but not limited to):
Once your application has been activated you may "lock" it to the computer. When activating, a computer ID number is generated from specific hardware of the PC and used to create the activation code. This computer ID is stored in the license once activated, and each time the application is run this computer ID is generated from the PC and compared to the ID in the license. If they do not match, the application will require re-activation.
More high-level information can be found in our blog: Product Activation: Fingerprints, Copy Protection, Disconnected Computers.
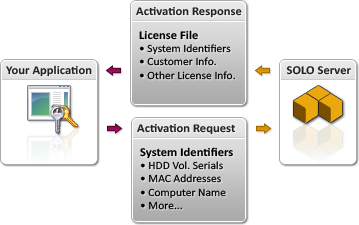
A system is authorized for a license during activation with SOLO Server. This allows SOLO Server to include the information about the system in the license file issued as illustrated below.

To further explain the illustration, here is the full process it depicts:
When activating an application through SOLO Server with the Enhanced Algorithms, the hardware related items that make up the Enhanced Computer ID are sent during the activation request. This create an Installation ID for that specific activation. Depending on your product option settings, you can configure SOLO Server to give another activation without decrementing the activation count if the user has not made any hardware changes since the original activation. For Product Options with Issue Installation ID enabled, check Allow Reactivations on Same Computer to enable this feature.
While you want to limit a license to only authorize a specific system, you also want to give a customer the flexibility to upgrade their system without invalidating the license. You can decide how much of a change in the identification of the system is allowed before it is no longer accepted as the same system.
Using a large amount of information about a system to authorize it has the benefit of allowing for more flexible matching fuzzy-logic (to allow some acceptable amount of change to occur without requiring a new activation) and allows you to better prevent other, very similar systems from being inadvertently authorized to use the same license file. However, collecting this kind of information could cause privacy concerns for your users. The system identification logic in Instant Protection PLUS 3 and SOLO Server relies on using hashes of information. Using the one-way cryptographic hashes prevents anyone and everyone from using data showing what hardware your customers use for anything other than the intended purpose (system authorization). Instant Protection PLUS 3 is not designed to enable you to use this data for purposes other than system identification and authorization for licensing purposes, and SOLO Server is also not designed to make this data useful or available outside of the intended capacity.